Hey there, super curious minds,
let’s be really honest here—if you’ve been working with microservices long enough, you’ve probably hit that point where everything feels like a group project with no team lead. Services yelling at each other across the cluster, authentication scattered everywhere, observability held together by logs and prayer, and your brain quietly whispering, “This was supposed to be better than monoliths?”
That’s where the idea of a service mesh sneaks in. It promises to solve a lot of those problems: better traffic control, resilience, security, observability—all packed into a neat, layered abstraction. It’s the glue between your services… or maybe the smart traffic cop, the bouncer, and the observability dashboard all rolled into one.
But what exactly is a service mesh?
Why is everyone in the Kubernetes ecosystem talking about it?
And more importantly: do you really need one?
In this article, we’ll break down the core concepts behind service meshes, including what they are, what problems they solve, and how they work under the hood. We’ll dig into control planes, data planes, proxies, and other buzzwords—but with a practical mindset (and hopefully, no tears).
No YAML dumps or complex install guides here—this is the conceptual groundwork. Think of it as your first casual conversation with the service mesh world before things get serious. Now let’s get started! 🎉
Microservices
In the past, applications were smaller, with fewer functionalities, and most of them followed a monolithic architecture. However, as businesses grew and applications became more complex, a new approach started to emerge. This shift was driven by challenges like handling dynamic traffic demands, improving observability, and ensuring better monitoring. As applications began to scale, companies needed a more flexible and efficient way to tackle these challenges. That’s where microservices architecture came into play.
In a monolithic architecture, the entire application exists as a single unit (a monolith). In contrast, a microservices architecture breaks down the application into smaller, independently deployable services, which communicate with each other using APIs.
Let’s consider an example: an e-commerce platform that features a main page for purchasing products, a payment page, a recommendation page, a customer care page, and so on. In a monolithic approach, the entire platform – including the main product page, payment gateway, recommendation system, customer care, and more – would all reside in one large application. Instead of this, with a microservices approach, we can break down the platform into individual services (or deployable units) for each functionality. This is similar to the “divide et impera” strategy that anyone familiar with data structures and algorithms has heard at least once in their life. Using this methodology, each service has a single responsibility. For our e-commerce platform, this makes maintenance easier and helps avoid the risk of introducing unexpected bugs with every update.
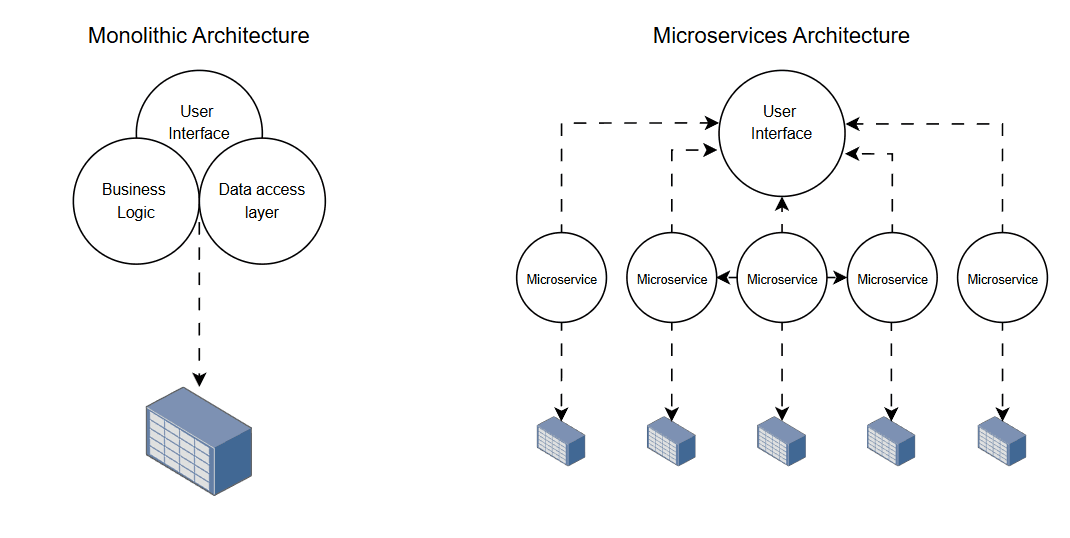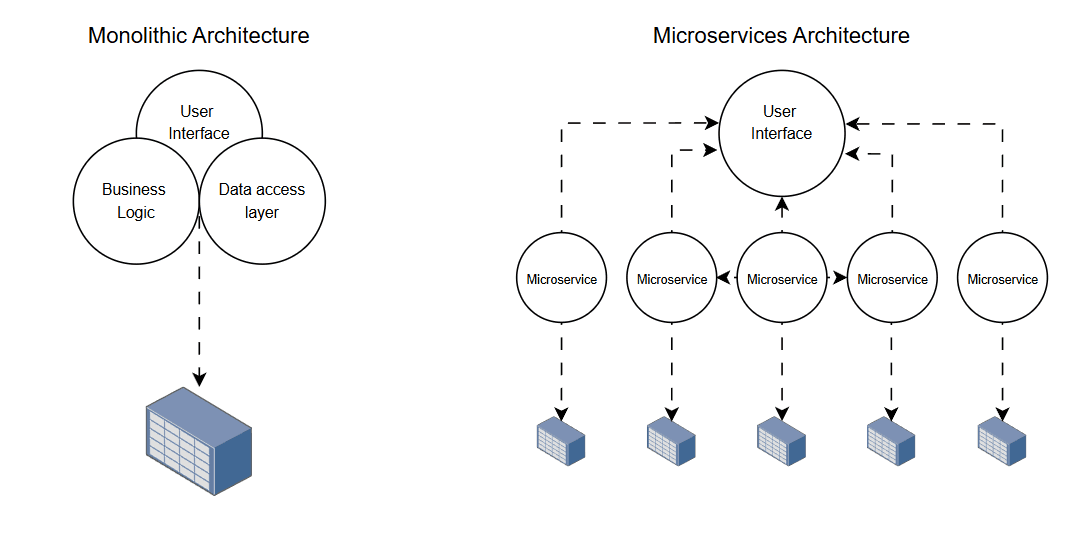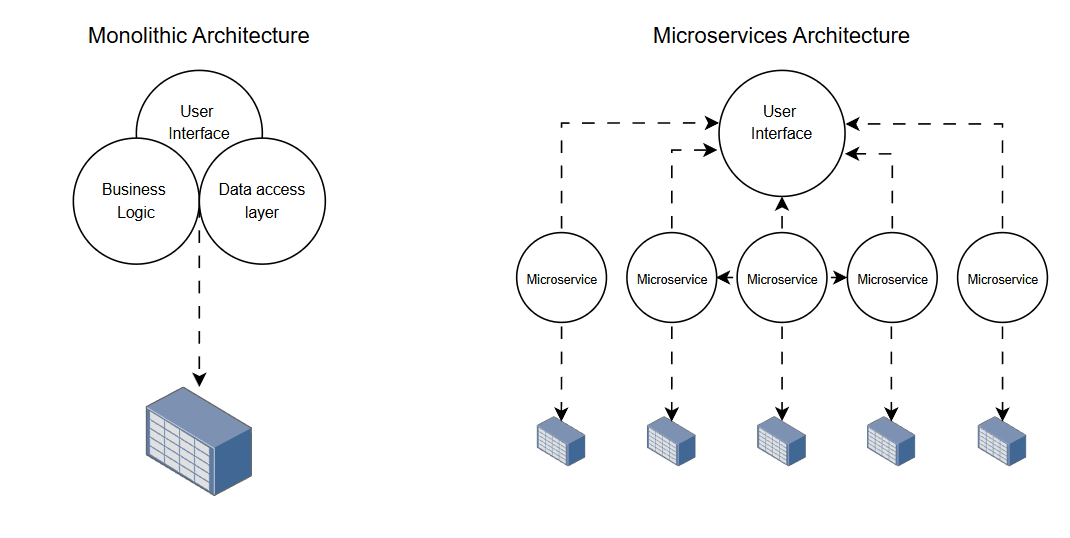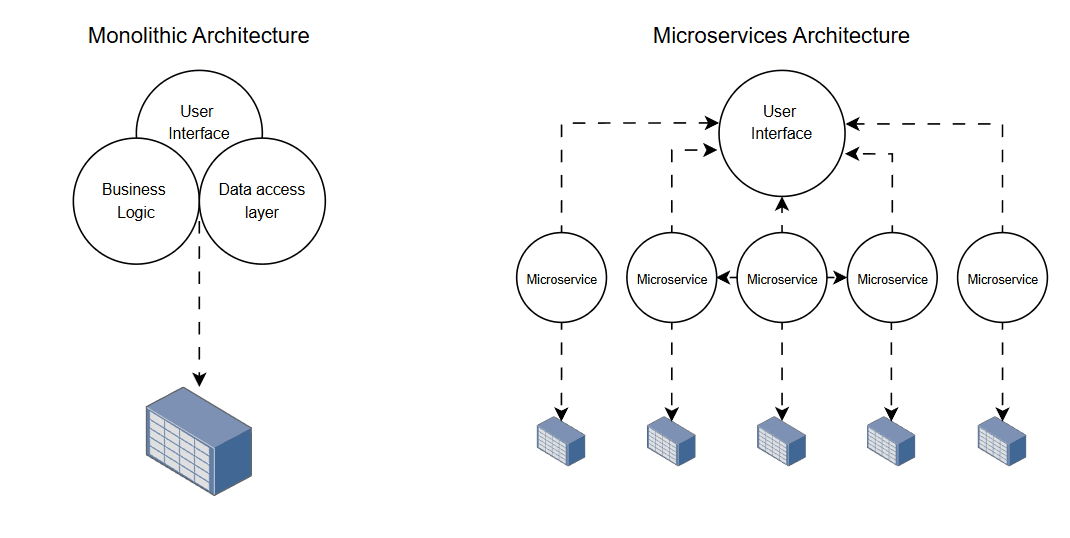 Image: Monolithic vs microservices architecture: in a monolithic architecture all the application is concentrated in one place while in a microservices architecture, every service is independent and can be easily maintained without influencing other services
Image: Monolithic vs microservices architecture: in a monolithic architecture all the application is concentrated in one place while in a microservices architecture, every service is independent and can be easily maintained without influencing other services
What is a service mesh?
When we talk about microservice architecture, we’re implicitly referring to a distributed environment where services communicate solely through APIs. In such an environment, a service mesh introduces an abstract infrastructure layer that manages service-to-service communication. It ensures efficient handling of service requests by controlling traffic, providing observability, enforcing security, and enabling service discovery.
Key components of a service mesh
The Control Plane is the heart of the service mesh. It coordinates the behavior of proxies and provides APIs for operations and maintenance teams to manipulate and monitor the entire network. This plane is crucial in the context of network design and cloud computing as it manages how data packets travel across the network.
Here, decisions are made regarding the routing of network traffic. On the other hand, the Data Plane is responsible for moving the data based on the routing choices made by the control plane.
The Control Plane performs several important functions:
-
Network Layout Management: It defines and manages the structure of the network.
-
Routing Tables & Traffic Flow: It updates routing tables and controls how traffic flows through the network.
-
Enforcing Rules: It ensures that network policies are followed.
Control planes are also common in traditional networking with protocols like OSPF and BGP. They are a key part of Software-Defined Networking (SDN) through centralized controllers and are managed by tools like Kubernetes in cloud computing to handle container orchestration.
The control plane ensures that the network operates smoothly and securely, optimizing the overall network performance.
Data Plane: Moving the Data
The Data Plane intercepts the communication between different services and processes it based on the decisions made by the control plane.
Key Tasks of the Sidecar Proxy
In a service mesh, the sidecar proxy is responsible for performing various key tasks:
-
Service Discovery: The sidecar proxy identifies all the available upstream or backend service instances.
-
Health Checking: It ensures the upstream service instances are healthy and capable of handling network traffic. This can be done through:
-
Active health checks (e.g., sending pings to a /healthcheck endpoint).
-
Passive health checks (e.g., detecting unhealthy states based on repeated 5xx errors).
-
Routing: Based on a REST request the proxy determines which upstream service cluster should handle the request.
-
Load Balancing: Once the appropriate service cluster is identified, the proxy decides which specific service instance should handle the request, including settings for timeouts, circuit breaking, and retry policies.
-
Security & Authentication : For incoming requests, the proxy verifies the caller’s identity using mechanisms like mTLS. It then checks whether the caller is authorized to access the requested endpoint. If not, the proxy returns an unauthenticated response.
-
Observability: The proxy generates detailed statistics, logs, and distributed tracing data for each request. This helps operators understand the flow of traffic across the services and troubleshoot any issues that arise.
Benefits of using a service mesh
-
Centralized Traffic Management: A service mesh allows for fine-grained control over communication between services, including advanced routing capabilities, retries, and failovers. This can be crucial in ensuring high availability and resilience.
-
Security at Scale: Security is paramount in microservices architecture, and service mesh addresses this by providing a uniform layer for implementing security measures like encryption, authentication, and authorization. It ensures that communication between services remains secure without burdening individual services with security concerns.
-
Resilience and Fault Tolerance: Service mesh introduces capabilities for implementing circuit breaking, retries, and timeouts, promoting resilience in the face of failures. It enables applications to gracefully handle faults, preventing cascading failures and ensuring optimal user experiences.
-
Enhanced Observability: Service mesh provides unparalleled visibility into the interactions between microservices. With features like distributed tracing and monitoring, organizations can gain insights into the performance and behavior of their applications, facilitating efficient troubleshooting and optimization.
But Wait… Why Not Use a Service Mesh?
Before we hand the service mesh the keys to our infrastructure, let’s pump the brakes.
Service meshes are incredibly powerful—but they’re also not free. Not in performance, complexity, or cognitive load. Here’s why you might not want one just yet:
- It’s Heavy: You’re adding sidecar proxies to every service. That’s more network hops, more memory, more CPU, and more configuration. You better have a good reason (or a beefy cluster).
- Steep Learning Curve: Control planes, mTLS, traffic shifting, retries… these are all good things, but they require real understanding and new operational tooling.
- Not Always Needed: If you’re running five services in dev with no real need for advanced routing or auth, a service mesh is like bringing Kubernetes to a shell script. Start with simpler tools and scale your complexity as needed.
- Debugging Becomes… “Fun”: That one sidecar proxy that failed to inject? That Envoy config you didn’t understand? Debugging service mesh issues can sometimes feel like playing 4D chess while blindfolded.
So no, a service mesh is not mandatory. It’s not a badge of honor. It’s a tool—and like any tool, you need to reach for it when and if it solves your specific problems.
Wrapping Up: The Mesh Is Only the Beginning
The service mesh world is vast, fast-moving, and—let’s admit it—a little intimidating. But if you’re building distributed systems, or just tired of duct-taping together retries, mTLS, and observability, it’s a space worth exploring.
In this first part, we’ve covered why service meshes exist, what they are, and when they make sense (or don’t). Hopefully, you’re walking away with a solid mental model, a few new questions, and a bit more clarity about what all the buzz is about.
Service meshes aren’t just a passing trend—they’re part of a broader shift toward smarter, more composable infrastructure. While the concepts can feel heavy at first, the payoff in resilience, visibility, and security is real.
Whether you’re just peeking into this space or already wrestling with sidecars and control planes, remember: you’re not alone._ And this journey?_ It’s only just begun.
In the next part of this series, we’ll dive into real-world implementations 🚀
Until then, keep your services chatty (but secure), your architectures simple (until they can’t be), and your curiosity sharp.
Mesh wisely. Stay tuned—and stay curious. 🌐🧩

